The Linux Storage, Filesystems, MM and BPF Summit recently hosted a session by Andrii Nakryiko, a distinguished engineer at Meta and a member of the eBPF Steering Committee, titled “Evolution of Stack Trace Captures with BPF” (video follows below). The talk delved into the advancements and future directions of stack trace capturing in BPF programs, highlighting both the current capabilities and the challenges faced by developers. Here’s a summary of the key points discussed:
1. Focus on Stack Trace Improvements
Nakryiko began by clarifying the scope of his talk, which was dedicated exclusively to improvements in stack trace capturing, deliberately excluding symbolization enhancements due to time constraints. His primary aim was to shed light on the evolution of stack trace captures within BPF programs.
2. Current API Limitations
Nakryiko detailed the existing APIs for capturing stack traces from BPF programs, emphasizing their limitations:
- Hash Collisions: The current system sometimes encounters hash collisions even with a small number of captured stack traces, leading to potential inaccuracies.
- Reusing Stack IDs: The automatic reuse of stack IDs, while efficient, can cause unexpected behavior in production environments. This issue was significant enough that Nakryiko and his team at Meta have disabled stack ID reuse to avoid related complications.
- User Space vs. Kernel Space: User space stack traces face additional challenges compared to kernel space stack traces. Kernel memory is always physically present, making kernel stack traces more reliable.
3. Automatic Stack Duplication
One of the notable features of the current API is automatic stack duplication. If the same stack trace is captured more than once, the kernel reuses the same slot and ID. This feature is beneficial in reducing redundancy but has significant implications, including potential hash collisions and unexpected behavior.
4. Proposed Improvements
Nakryiko proposed several improvements to enhance stack trace capturing:
- Ring Buffers for Notification: Utilizing ring buffers to send notifications about stack trace readiness could streamline the process, allowing for dynamic memory allocation and better management of stack traces.
- Dynamic Memory Allocation: Moving away from fixed-size arrays to dynamically allocated memory could help manage stack traces more efficiently and reduce the likelihood of hash collisions.
- Reliable Kernel-Provided Stack Trace Capture: Emphasizing the need for a robust kernel-provided stack trace capture as a basic building block to simplify stack trace management and improve reliability.
5. User Space Considerations
Addressing user space handling, Nakryiko discussed several strategies:
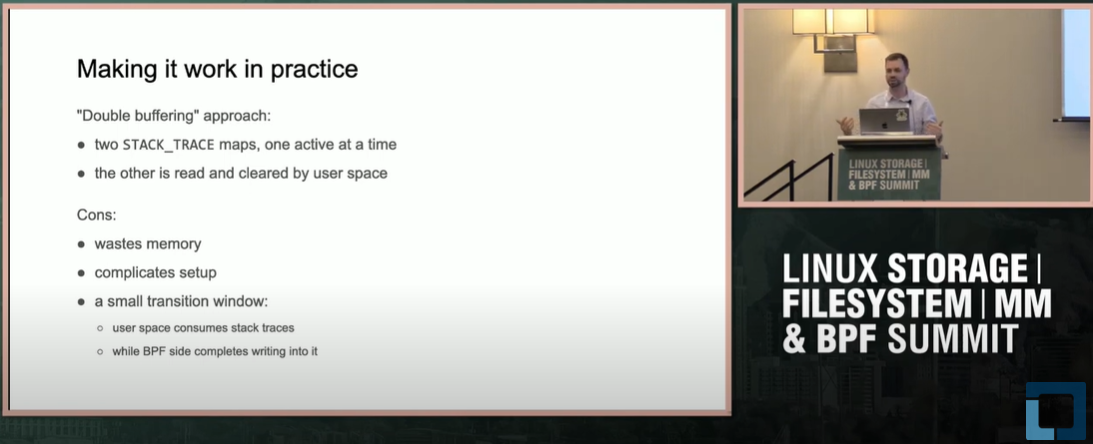
- Double Buffering: Using double buffering techniques to allocate two identical stack trace maps, designating one as active and the other as being consumed by user space, to minimize hash collisions.
- Avoiding Stack ID Reuse: Advising against reusing stack IDs to prevent unexpected issues and ensure more predictable behavior.
- Custom BPF Programs and Work Queues: Suggesting the use of custom BPF programs and work queues to handle stack trace processing more effectively, allowing for greater flexibility and efficiency.
Nakryiko’s session provided valuable insights into the evolution and future of stack trace capturing in BPF programs. By addressing the current limitations and proposing thoughtful improvements, Nakryiko aims to enhance the reliability and efficiency of stack trace captures, benefiting developers and production environments alike. As BPF continues to evolve, these advancements will play a crucial role in optimizing performance and debugging capabilities within the Linux ecosystem.